Top 15+ Information Security Thesis Topics
Information security is nothing but safeguarding web-based information from unauthenticated network devices and users. Majorly, it is intended to provide data safety, reliability, Secrecy, trust, and accessibility for the authenticated devices/users.
For the purpose of data protection, it concentrates on special information security policies and strategies. These policies ensure to shield the data against interruption, illegal access, alteration, and revelation. In the following, we have mentioned the core processes involved in information security.

Key Processes in Information Security
- Safe Storage
- Protect the network information against both internal and external attacks and store them securely
- Assure the trust and privacy for stored data
- Protected Data Communication
- Validate the identity of the communication devices
- Ensure the network information privacy and reliability
- Assure the security over components connected in the network
- Resistant by Tampering
- In exiting, the attackers easily hack the network and access the system data. So, the efficient approach is needed to get back the control of attackers
- Secure Software Development Environs
- Provide secure sophisticated platform for system design in contradiction of unpredictable services and system
- User Recognition
- Verify the user identity for resource accessibility through several techniques
- For instance: Authenticate the user by personal password or pre-shared key
- Content Protection
- Guard the system content against sudden undesirable hackers, attacks, intruders and viruses.
- Identity Controlling
- Recognize the each and every system by their unique features
- Manage the resource accessibility based on the authenticated user privileges along with their constrains
- Protected Network
- Distribute requested services only to the authenticated users / devices
- Block the resource or network accessibility of the illegal users/ devices
Our research guidance will best suit your needs if you’re looking for qualified expert guidance. Our experts are frequently updating their skills on current research developments in information security thesis topics. So, we are ready to support you in tackling all the research challenges. Here, we have listed out few common threats that are evolving in information security.
Different Kinds of Security Attacks
- Device Attacks
- Fault Injection based
- Abuse and delay the data which is actively driving the defective functions to perform
- For instance: Fault injection (based on Electromagnetic, CPU Frequency and Voltage)
- Side Channel based
- Abuse and delay the data which is passively collected and monitored from the network entities
- Fault Injection based
- Topology Attacks
- Underlying Structural design:
- Improper manipulation of fundamental features while development of TrustZone
- For instance: device sleep mode and bug fixing methods
- Unemployed Security Factors:
- It refers the characteristics that are not properly utilized for security purpose
- For instance: pointer based data sanitization and downgrade resilience
- Underlying Structural design:
- Application Attacks
- Poor Utilization of Cryptography:
- It is kind of attack that leads to data insecurity because of utilizing weak cryptographic techniques
- For instance: digest methods and weak authentication
- Logic oriented:
- It is kind of attack that cause due to the logical errors
- For instance: mismatch data type and ineffective data assessment
- Buffer oriented (Overread and Overflow):
- It is kind of attack that affect the memory of the system
- For instance: buffer overhead, buffer underflow and buffer overflow
- Poor Utilization of Cryptography:
In this project, we have addressed the latest Information Security Thesis Topics along with their research directions!!!
What are the 3 elements of layered security?
Now, we can see the layered security in the network since the data is communicated over the network through different layers. So, it is essential to secure those layers for the privacy of transmitting data.
In specific, the layered security approach is designed to focus on overlying layers. Here, we have mentioned three main entities that are required to maintain safety for overlying layers. They are the detection layer, correction layer, and prevention layer. Further, we have specified add-on layers in the network security.
- Prevention Layer
- Penetration Analysis and Testing
- Advanced Access Control
- Continuous Credential Modification
- Secure Information Backup and Storage Hardware
- Safety of Physical Components
- Trust based Information Privacy and Approachability
- Biometric based Multi-factor User Identification
- Authentication and Authorization of Network entities
- Detection Layer
- Firewall
- Honeypots
- IDS and IPS
- Security Information And Event Management (SIEM) Software
- Anti-malware
- Correction or Response Layer
- Data Backup and Recovery
- Intrusion Prevention System (IPS)
- Instigate Alternative Input Devices
- Identification and Matching of Attack Signature
- Regular Firewalls Policies Updates
Some other layers in information security can be follows,
- Application Layer
- Secure Data Confidentiality
- Authenticated Key Exchange
- Support Layer
- Anti-Virus and Anti-Malware
- Secure Cloud based Intelligent System
- Network Layer
- Improved Cryptographic Techniques
- Network Enmities (user and device) Authentication
- Perception Layer
- Sensed Information Security and Privacy
- Private Key Agreement and Distribution
As the research team, our development team also works efficiently in implementing any sort of research solution despite complications. Below, they have mentioned some significant approaches that are used for modern security models modelling a novel research proposal.
Important Functions of Information Security Thesis Topics Model
- Determine the security risk mitigation techniques
- Continuously observe the network actions and do needed modification for enhancing the security
- Detect the data extortions, susceptibilities and other security related issues
- Need to assess the risk activities that affect the data
- To the end of implementation, check whether the following questions are answered in your security system
- What kind of process did the user do?
- Which strategies are followed to access the network amenities?
- Who are the users have network data accessibility rights?
- Select the optimum result yielding security approaches and apply them in required phase of development
In addition, our developers have also suggested other important techniques used to untie the challenging security issues like threats and vulnerabilities. Beyond this, we let you know other vital techniques based on your project needs. Also, we assure you that we will support you to the fullest till the end of the project with expected results.
- Proactive Defences Strategies
- Attack Hypothesis Testing
- Security Mechanism Assessment
- Perfect System Maintenance
- Detection of Security Vulnerability
- Attack Identification Functions
- Attack Recognition
- Proactive and Reactive Defences
- Decision Making Validation
- Persistent Retraining Models
- Defensive Measures against grey-box / black-box Attacks
- Randomization
- Enhanced Ensembles Classifier
- Data Hiding and Encryption
- Preventive Measures against white-box attacks
- Attack Identification
- Adversarial Reinforcement Learning
- Strong Machine and Deep Learning Approaches
Our experts have itemized the highest-demanding research notions in the information security field for your awareness of current Information Security Thesis Topics. More than this, we are furnished with a wide range of interesting topics to serve you in all respects.
Top 15 Information Security Thesis Topics [Research Ideas]
- Secure Remote Healthcare Application
- Enhancing Security using effective Access Control Strategies
- Modelling of Reputation assisted Trust Systems
- De-Anonymization Approach for Secure Data Mining and Analytics
- Intrusion Prevention and Detection System
- Novel Computation Mechanisms for Preserving Secrecy
- Innovative Structural design of Cybersecurity Models
- Blockchain based Cross‐Domain Trust Assessment
- Artificial Intelligence-aided Trustable Inference System
- Real-time Improved Safety Application in HetNet-IoT
- Lightweight Multi-Factor authentication in IoT Networks
- Secure Data Aggregation and Mining Technologies
- New Development of Automated Security Mechanisms
- Adaptive Anonymity Approach for System Privacy and Security
- Trust enabled MAC and application layer protocols for Network Security
- Secure Key Generation and Distribution in Edge-Fog computing
Then for development, we have recommended few widely used tools for information security. These tools are listed based on the specific operations involved in information security along with their unique characteristics.
Information Security Monitoring Tools
- Data Auditing Tool
- Argus (real-time simulation, multi-platform)
- Packet Capturing Tools
- Snoop (0% packet loss, offer > 12 choices)
- Ethereal (Easy to use and robustness)
- Net2pcap (Support auditing service and Linux-oriented)
- Tcpdump (Low interference in compare to ethereal)
- Gulp (Very powerful and user-friendly)
- Ngrep (Support massive data and Cross-layer)
- Libcap (Very efficient)
- Aimsniff (Support Linux platform)
- Packet Analyser Tools
- IPgrab (Presentation of packet header)
- Karski (Restricted appropriateness)
- Nfdump (Friendly packet inspection)
- Packet Sniffing Tools
- Dsniff (Support Unix platform)
- Angst (Powerful and user-friendly)
- Password Recovery Tool
- Cain and able (user-friendly)
- Traffic Analysis Tools
- Nast ( Resourceful and provide > 12 choices)
- Tcptrace (Powerful and Popular)
- TCPtrack (Support linux platform and TCP study)
- Man-in-middle Attack Tools
- Ettercap (Competent, enable > 35 choices)
- Data Flow Visualization and Capturing
- Nfsen (Smooth network data flow)
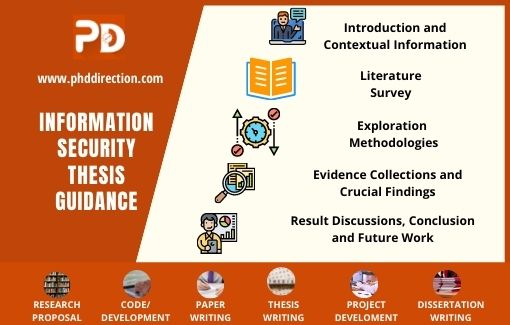
How to structure a thesis for effective writing?
When we talk about thesis writing, it is necessary to confirm the thesis format/structure. Since it only gives the first impression of the thesis before start reading the thesis by forming encapsulated information with fine-tuned alignment.
Our native writers strictly follow the pre-defined rules that help to uplift the thesis quality by knowing this importance. Basically, for all Information Security Thesis Topics, we usually follow the below chapter, which may change based on the institute’s requirement.
Here, we have given the common information that must address in perfect thesis writing.
- Introduction and Contextual Information
- Start with the precise thesis statement which address the research objectives
- Describe the sufficient background context for better understanding of the concept
- Explain the detailed introduction about the research that further going to discuss in whole thesis
- Denote the research topic in short and crisp with clear insight
- Literature Survey
- Intelligently move on to the literature survey
- Discuss the examined recent previous research work related to the concept
- Figure out the merit and demerits of the exiting methodologies and algorithms
- Pin point the research gaps that are not addressed properly
- Exploration Methodologies
- Perform qualitative and quantitative study
- Use appropriate methodologies, techniques and algorithms for solving the problem
- Address the used numerical or mathematical functions
- Present the obtained experimental results
- Evidence Collections and Crucial Findings
- Signify the data gathered while analysing process
- Surely address the minor and major evidence and proofs
- Prove the research objective
- Result Discussions, Conclusion and Future Work
- Discuss the achieved research outcome in conclusion
- Write overview of the research findings
- Give the future research possibility and directions
On the whole, we are ready to give end-to-end research assistance in PhD/MS study. And, we also support you to build information security thesis topics, if you are curious about knowing other new technologies reach our expert team.
Why Work With Us ?
Member Book
Publisher Research Ethics Business Ethics Valid
References Explanations Paper Publication
9 Big Reasons to Select Us
Senior Research Member
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Research Experience
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
Journal Member
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
Book Publisher
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Research Ethics
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Business Ethics
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Valid References
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Explanations
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Paper Publication
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.